The year 2018 has seen a surge in cryptocurrency-mining malware by four times in the Middle East, Turkey, and Africa (META) regions according to anti-virus firm Kaspersky Lab. Some 13 million cases were registered around the world for such malicious software infections that redirect a portion of the host’s computer processing power towards mining cryptocurrency for the guest. A four-time increase from 3.5 million cases back in 2017.
It’s important to know that there are two types of cryptojacking:
1) The first one involves mining software injected directly into the host’s computer files. They’re usually delivered by malicious links and through some form of scamming or deceit.
2) The second type refers to in-browser mining scripts that run as long as the visitor stays on the page. Some are legitimate mining scripts installed by their respective website owners, while others are malicious scripts injected by third-party actors. The former is considered the safest form of cryptojacking, being approved by the website owner, while the latter exploits both the website and its viewers. Most of the hidden scripts were injected into streaming websites, especially pornographic or pirating sites, forums, and similar places where the user is inclined to spend much time.
![file-20180406-5578-1w5ge27[1]](https://cryptoworldaffairs.com/wp-content/uploads/2018/12/file-20180406-5578-1w5ge271.png?w=1040)
The source code on a cryptojacking website with the beneficiary wallet address. Screenshot author Pranshu Bajpai, CC BY-ND
Some might argue that almost all cryptojacking cases are unethical, thus the name ‘jacking.’ The embedded mining software is almost never brought to the attention of the visitor but instead happens secretly, without disclosure — everything at the expense of the user who may not even realize that his processing power and electricity are being spent to create and send cryptocurrency to an unknown wallet. It’s fundamental to keep in mind that even if unnoticeable, the mining process drains the battery, consumes electricity, and works the processor and video card which in turn, can make the system run slowly, reduce its life-span, or even damage the hardware by overloading.
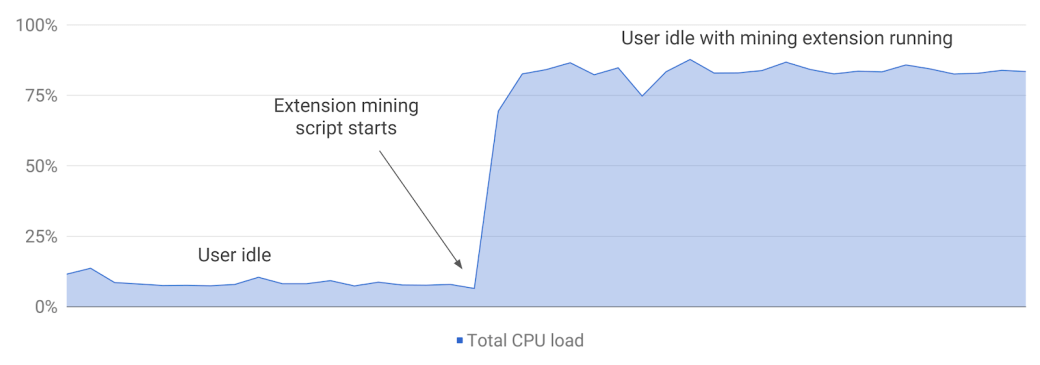 An example of CPU overutilization from hidden cryptocurrency mining in an extension
An example of CPU overutilization from hidden cryptocurrency mining in an extension
Although the whole world is affected by the attacks, less-developed countries from Africa, South America, and the Middle East seem to experience the majority of the attacks.
According to a study made by Bad Packets Report on February 2018, it showed that 34,474 websites are executing Coinhive, the most popular cryptojacking JavaScript. Another research from AdGuard found that the total profit from cryptojacking is around $150,000 per month from which a third goes to the mining network and the rest to the website owner.
There are some exceptions to the rule, however — cases in which websites ask for the clear consensus of the user in using some of its processing power to generate cryptocurrency. Transparent cases such as these are considered legitimate and safe. For example, this UNICEF website asks your permission to mine cryptocurrency off your browser for charity.
Although the mining scripts are merely tools that can even serve a useful purpose, as mentioned above, the situation got out of hand. A few months ago, Google announced a general ban on all plugins and extension involving cryptocurrency mining from its Chrome browser, whether white or black hat.
“Until now, Chrome Web Store policy has permitted cryptocurrency mining in extensions as long as it is the extension’s single purpose, and the user is adequately informedabout the mining behavior. Unfortunately, approximately 90% of all extensions with mining scripts that developers have attempted to upload to Chrome Web Store have failed to comply with these policies, and have been either rejected or removed from the store.”
Individuals are not the only ones targeted: businesses are too. Company-owned computers are very sought-after targets since they’re continually functioning in large numbers and usually lacking adequate security protocols. More so, hackers have adapted the script-injection methodology specifically for commercial companies through ‘formjacking.’ It refers to a malicious Javascript inserted into the payment process of a website. The credit card information is then obtained. Most recently, in June 2018, Ticketmaster had 40,000 customer records compromised, and in September 2018, British Airways encountered a similar attack on 400,000 clients.
As a first defense system, the National Cyber Security Centre’s board toolkit is an excellent starting point. Adblockers, antivirus programs, and mining-blocking browsers are must-haves against cryptojacking.
SOURCES:
http://theconversation.com/cryptojacking-spreads-across-the-web-94088
https://badpackets.net/how-to-find-cryptojacking-malware/
https://blog.chromium.org/2018/04/protecting-users-from-extension-cryptojacking.html

![BoxmitExtasy[1]](https://cryptoworldaffairs.com/wp-content/uploads/2018/12/BoxmitExtasy1.jpg?w=340&h=604)
![Waschmaschine2[1].jpg](https://cryptoworldaffairs.com/wp-content/uploads/2018/12/Waschmaschine21.jpg?w=340&h=602)
![Ecstasy-Tabletten2[1]](https://cryptoworldaffairs.com/wp-content/uploads/2018/12/Ecstasy-Tabletten21.jpg?w=1040)
![91d2376d-acf0-47bf-8849-9b1d0302eb57-Christian_Maire[1]](https://cryptoworldaffairs.com/wp-content/uploads/2018/12/91d2376d-acf0-47bf-8849-9b1d0302eb57-Christian_Maire1.jpg?w=257&h=321)